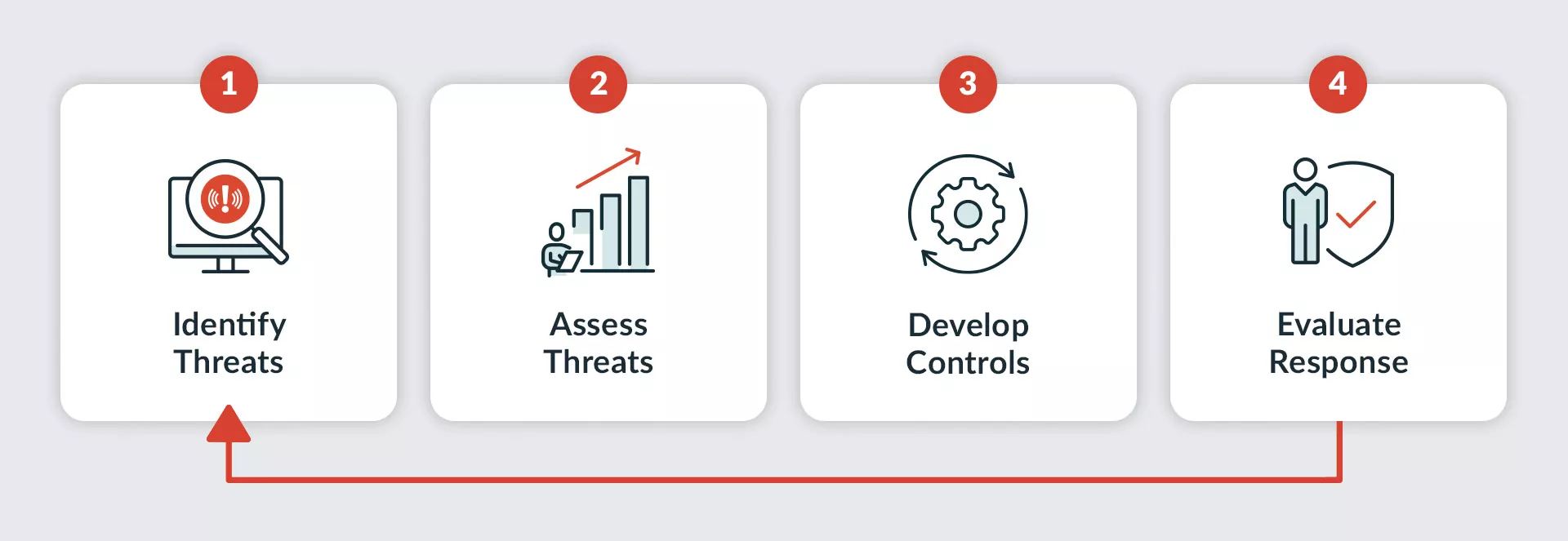
4 Steps to Conducting a Business Threat Assessment
Preparation is Key!
Page Contents
Contrary to popular belief, your organization <em>is</em> susceptible to falling prey to threats such as cyber-attacks as well as various other security breaches. What’s more, threats can come in multiple forms from physical such as weather hazards to digital.
How Necessary is a Threat Assessment?
- Without an assessment you have no idea how you will fare against threats
- How can you prepare for or protect yourself against something you you’re unaware of?
Be Aware of Your Assets
Are you aware of what needs protecting? Having a clear idea of the assets you possess will help you anticipate and narrow down the types of threats are likely to face. As previously mentioned, many companies are constrained to safeguarding sensitive information. Personally identifiable employee information such as social security numbers and even financial information is all data that is at risk of leaking if not properly protected. Not only could such a data breach result in legal trouble but it could give your competition a significant advantage and that’s without even going into the how much of an inconvenience this will be to your business.
Each business is different, it’s likely you will be faced with threats specific to your industry so pay attention to its landscape, what type of threats are popular or is your competition falling victim too? Learn from their mistakes while forging your own strategies. Detractors will likely put you in the same boat as your competition, if they are being targeted so will you and most likely towards the same ends.
What percentage of companies in your industry have experienced security breaches? Who are their customer base? For what type of data? Can your employees impact your security measures? If your organization was put in the same scenario, how would it do? Simply asking and answering these questions will help you establish whether or not you have the infrastructure in place to respond to the ongoing threats.

Time to Start Planning
Okay, now you’re aware of your assets, you’ve assessed your vulnerabilities as well as what they are so, what the plan? Now you have all the elements you need to come up with a plan and policies. It’s probable you will have to coordinate different segments of your organization from leadership, to IT and more to effectively install this plan. Favor simple and flexible policies that can be easily adjusted making sure they evolve with the course of time.
Success Lies in Execution
Ensuring all parts of your organization are equipped, prepared and informed to deal with the threat is important. Steps such as employee training and regular meetings to reinforce company policies is important as the more members within your infrastructure are informed the better of you will be. Furthermore, calling on tools such as mass notification systems to effectively communicate to everyone of incoming threats in a timely manner will save you many headaches.